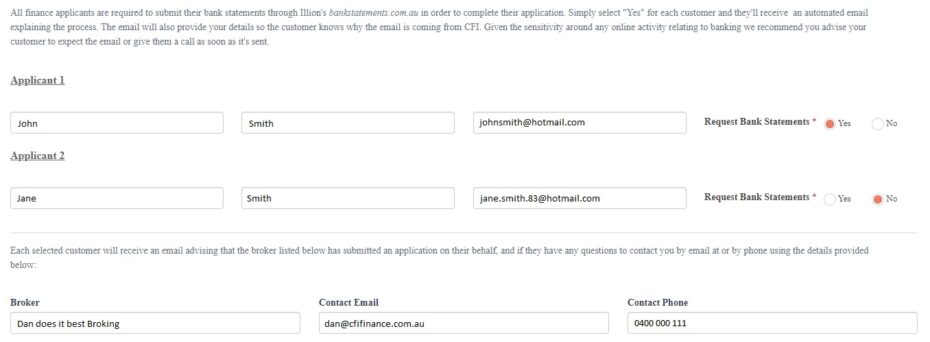
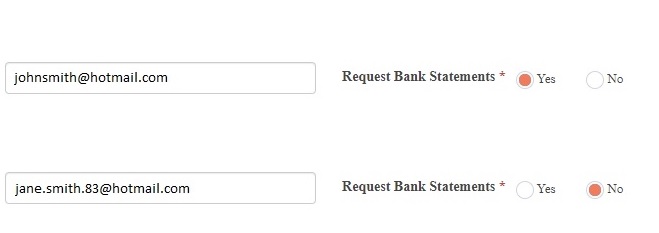
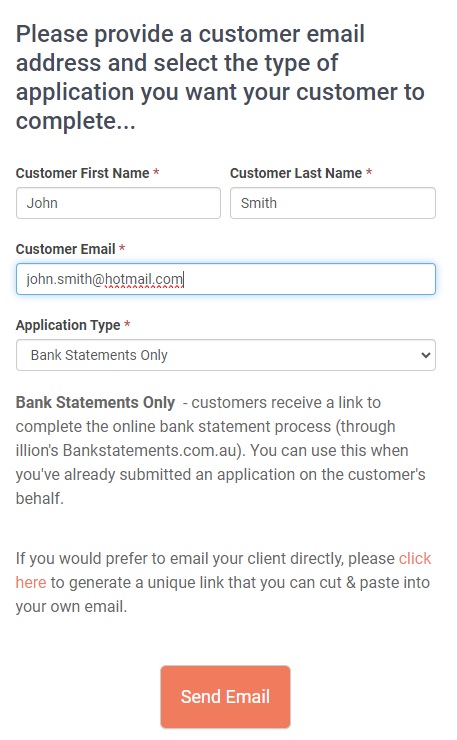
Most of the time Financial Statements represent business performance on an annual basis, as at a given balance date. (As mentioned previously Management Accounts might be more recent and may be requested if a lot of volatility between years is expected, or if formal accounts are more than 6 months old).
So, with the above in mind, what can the Financial Statements tell us? In many cases quite a lot. Firstly, as financial statements will usually provide a comparison to the prior year, we can look at what’s stable and what’s not. Is revenue up or down? What about expenses? Have they moved in line with revenue? What are the business borrowings? Is it asset rich and cash poor? Let’s dive a little deeper…
The Balance Sheet
The balance sheet presents the assets and liabilities of the business, split into two key groups, current and long-term, and in simple terms results in equity (assets minus liabilities).
Assets represent what the company owns and include tangible assets like property, equipment, and inventory, as well as intangible assets like patents and goodwill.
Liabilities encompass what the company owes to external parties, such as loans, accounts payable, and accrued expenses.
Equity is the result we get from deducting the liabilities from the assets. It comprises common stock, additional paid-in capital, retained earnings, and other comprehensive income.
Some key information from the balance sheet can also be used to calculate common ‘ratios’ that can give insights or indicators around business health, we’ll look at these in more detail shortly. At first glance though some key questions can be asked (and hopefully answered).
Solvency & Liquidity – Solvency refers to the ability of a business to meet its financial obligations in the long term, for example a business may be owed a lot of money by its customers and in turn may owe money to its suppliers. In simple terms we might say that the business is solvent if it is owed more than it in turn owes to others. Liquidity on the other hand refers to the ability of a business to meet its obligations in the short term, generally this means cash and liquid assets such as stock vs. short term debt.
Aged Debtors
On paper a business can appear liquid, but if a significant portion of the current assets of the business are debtors instead of cash it can be useful to review an Aged Debtors report. This shows all the debts that make up the amount owed to the company, breaking down who owes how much, and how long they’re taking to pay. Liquidity and even solvency can often depend on just a few large debtors, so it pays to make sure that customers are paying. This is particularly relevant for service based businesses or those in the construction industry.
Profit & Loss Statements
The P&L sets out the revenue and expenses of the business for the period, resulting in either a profit or loss.
At the top of the report we start with revenue which shows the income of the business from its core activities, such as sale of products, as well as revenue from other sources if applicable. For some types of businesses, it’s also common to see the ‘cost of sales’ deducted from Gross Revenue, yielding a Net Revenue amount before the rest of the business operating expenses are deducted ‘below the line’.
Expenses show all the costs incurred by the business in the period including operating expenses, depreciation, and interest expenses.
The resulting profit or loss might be shown in a few different ways, each slightly different:
- EBIT (Earnings before Interest and Tax) – Net Income before paying income tax and with interest costs removed.
- EBITDA (Earnings before Interest, Tax, Depreciation and Amortisation) – Similar to the above, but with depreciation and amortisation also removed, this is a common measure for businesses that have a large number of fixed assets.
- NPBT (Net Profit Before Tax) – A more simplistic measure of net profit, interest and depreciation are included in this amount.
- NPAT (Net Profit After Tax) – A very simple measure, after everything is said and done, how much did the business make or lose?
All of the above can provide significant insights into business performance. Is revenue stable or increasing? What does the business spend its money on? Is it profitable? Is it drowning in interest costs or showing a profit only through abnormal income? Do costs align to those of other similar businesses? Does it make money?
The Cash Flow Statement
To really get your finger on the pulse of a business, a cash flow statement can be exceptionally useful (although this is often now being superseded somewhat by digital bank statement downloads which can often provide a more detailed and up-to-the-minute picture of cash movement).
The cash flow statement shows cash coming in and out of the business over time, usually broken down by month and grouping cash into operating, investing, and financing activities.
Key elements of the cash flow statement include:
- Operating Activities: Showing cash flows from the company’s primary operations, such as receipts from customers and payments to suppliers.
- Investing Activities: Showing cash relating to the acquisition and disposal of long-term assets, such as property, plant, and equipment.
- Financing Activities: Showing cash movements relating to obtaining or repaying debt, raising equity, or paying dividends.
All of this information can help a lender (or broker) understand a company’s cash-generating capabilities, liquidity position, and most importantly its ability to meet its financial obligations.
Ratios
To wrap up this little primer, let’s look at some of the key ratios that analysts use to get a handle on business health, and the relevance of each one. These quick calculations can provide a useful benchmark, but as with everything the devil is in the detail, so it pays to make sure that the ratios you’re looking at make sense for the type of business you’re dealing with.
- Current Ratio: The current ratio is all about liquidity, measuring a company’s ability to meet its short-term obligations with its short-term assets. It assesses the company’s liquidity position by comparing its current assets to its current liabilities.
- How it’s calculated? Current Ratio = Current Assets / Current Liabilities
- Why it’s relevant: A high current ratio indicates that a company has more current assets than current liabilities, suggesting strong liquidity and the ability to cover short-term obligations. Conversely, a low current ratio may indicate liquidity issues and difficulty meeting short-term liabilities.
- Example: If a company has current assets worth $500,000 and current liabilities amounting to $300,000, the current ratio would be 1.67 ($500,000 / $300,000), indicating that the company has $1.67 in current assets for every $1.00 of current liabilities.
- Quick Ratio: Also known as the acid-test ratio, the quick ratio is a more stringent measure of liquidity compared to the current ratio. It excludes inventory from current assets since inventory may not be easily convertible to cash in the short term.
- How it’s calculated? Quick Ratio = (Current Assets – Inventory) / Current Liabilities
- Why it’s relevant: The quick ratio provides insight into a company’s ability to meet its short-term liabilities using only its most liquid assets. It offers a conservative assessment of liquidity, particularly relevant for businesses with slow-moving inventory.
- Example: If a company has current assets of $500,000, including $100,000 in inventory, and current liabilities of $300,000, the quick ratio would be 1.17 ([$500,000 – $100,000] / $300,000), indicating that the company has $1.17 in liquid assets for every $1.00 of current liabilities.
- Interest Cover: The interest cover ratio, also known as the ‘times interest earned’ ratio, measures a company’s ability to meet its interest obligations on outstanding debt. It assesses the company’s profitability relative to its interest expenses.
- How it’s calculated? Interest Cover = Earnings Before Interest and Taxes (EBIT) / Interest Expenses.
- Why it’s relevant: A higher interest cover ratio indicates that the company generates sufficient earnings to cover its interest payments comfortably, signifying financial stability and lower default risk. Conversely, a low interest cover ratio may indicate financial distress and an increased risk of default.
- Example: If a company has EBIT of $500,000 and incurs $100,000 in interest expenses, the interest cover ratio would be 5 ($500,000 / $100,000), indicating that the company’s earnings cover its interest expenses five times over.
NB: It’s worth noting that Interest Cover does not necessarily equate to servicing, as loans often require both principal and interest payment which both consume cash, but this ratio deals only with the interest portion.
- Gearing: Gearing, also known as leverage, measures the proportion of a company’s capital that is financed by debt relative to equity. It assesses the company’s financial risk and indicates the extent to which it relies on debt financing.
- Why it’s relevant: A high gearing ratio suggests that the company is heavily reliant on debt financing, increasing its financial risk and susceptibility to economic downturns. Conversely, a low gearing ratio indicates a conservative capital structure with lower financial risk.
- How it’s calculated? Gearing = (Total Debt / Shareholders’ Equity) x 100%
- Example: If a company has total debt of $2,000,000 and shareholders’ equity of $3,000,000, the gearing ratio would be 66.67% ([$2,000,000 / $3,000,000] x 100%), indicating that 66.67% of the company’s capital is financed by debt.